Have you ever paused and genuinely asked yourself: How safe is cryptocurrency, really?

In a digital world constantly bombarded by hacks, scams, and cyber threats, committing your hard-earned money to a purely digital asset—a set of numbers and letters—might feel like a monumental leap of faith. After all, there’s no central bank to call, no physical vault to protect the assets, and no government insurance to fall back on.
This is precisely where the genius of Blockchain Technology steps in.
Blockchain is not just a complicated buzzword for tech enthusiasts; it is the very essence of trust and the bedrock of security in the entire crypto space. It’s the invisible, unbreakable backbone that allows Bitcoin, Ethereum, and thousands of other digital currencies to exist and transact globally without the need for traditional, centralized intermediaries like banks, PayPal, or credit card companies. When you own crypto, you are fundamentally trusting this ingenious technology.
Why is this level of security so critically important? Because cryptocurrency operates on the revolutionary principles of permissionless and trustless transactions. This means anyone, anywhere, can send or receive value, and no single person, company, or government needs to verify or sanction the transaction. The system itself is self-policing.
In this deep dive, we’ll unlock the secrets of this digital fortress. We will explore how the four fundamental pillars of blockchain—its Distributed Ledger, its powerful Cryptography, its clever Consensus Mechanisms, and its defining Immutability—combine to forge a system that is virtually impossible to corrupt, ensuring the integrity and safety of your digital money.
Part 1: Security by Spreading Out (Decentralization and the Distributed Ledger)
To appreciate blockchain’s security, you must first understand its revolutionary structure.
Think about a traditional financial ledger, like the one used by your bank. All transaction records are kept in one central location—a highly protected server farm controlled by the bank. While these are secured with layers of firewalls, if a determined hacker manages to breach that one central server, they gain access to and can potentially alter all the data. This creates a Single Point of Failure.
Blockchain completely flips this outdated model on its head. It is a Distributed Ledger Technology (DLT). Instead of one vault, imagine millions of identical, interconnected vaults spread across every continent.
The Power of the Network
- Decentralization is the Defense: When a new cryptocurrency transaction occurs, it isn’t sent to one bank; it’s broadcast to every computer (or “node”) across the global network simultaneously. There is no central governing body.
- Collective Verification: Each node in the network independently verifies the transaction to ensure its legitimacy. They check that the sender actually owns the crypto they are trying to send and that the transaction follows all network rules.
- Data Redundancy: Critically, every single node maintains its own identical copy of the entire transaction history, going all the way back to the very first block (the Genesis Block).
This redundancy is the core defense mechanism. If a malicious entity attacks one server and changes its data, the other millions of nodes instantly see the discrepancy, reject the fraudulent version, and continue operating with the correct, consensus-approved data. To successfully corrupt the system, a hacker would need to simultaneously attack and compromise over 51% of the entire global network’s computing power—an undertaking so vast and expensive it is, for major blockchains like Bitcoin, economically impossible. The sheer size and global spread of the network make it the most powerful security layer.
Part 2: The Unbreakable Lock (Cryptography and Digital Keys)
The next major layer of security is built using advanced mathematics, specifically Cryptography—the science of secure communication. This is what gives cryptocurrency its name.
Blockchain uses a two-pronged cryptographic approach: Public-Key Cryptography for ownership and Hashing for data integrity.
Public and Private Keys: The Digital Identity
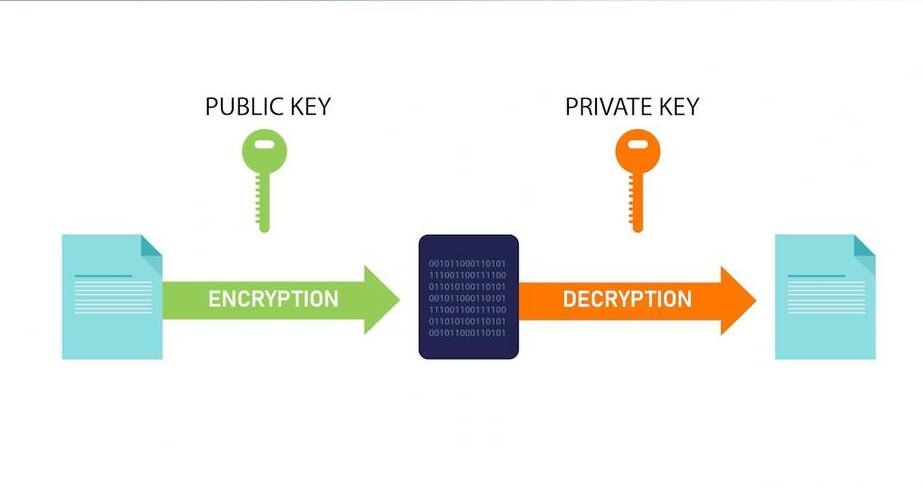
Every user on a crypto network has a pair of digital keys:
- The Public Key: This is your wallet address—think of it as your bank account number. You can share this with anyone, as it only allows people to send crypto to you. It is publicly visible on the blockchain.
- The Private Key: This is your secret password—think of it as the PIN code for your digital vault. It is a highly complex, random string of characters that is mathematically linked to your Public Key. This key is used to create a digital signature to authorize or “sign” transactions.
The Security Advantage: Without your Private Key, it is mathematically impossible for anyone to move your cryptocurrency. The funds are locked in your address until you use your private key to digitally sign a transaction. Therefore, the single most crucial rule in crypto is: Never share your Private Key. Losing it means losing your funds; sharing it means losing control of your funds.
Hashing: The Digital Fingerprint
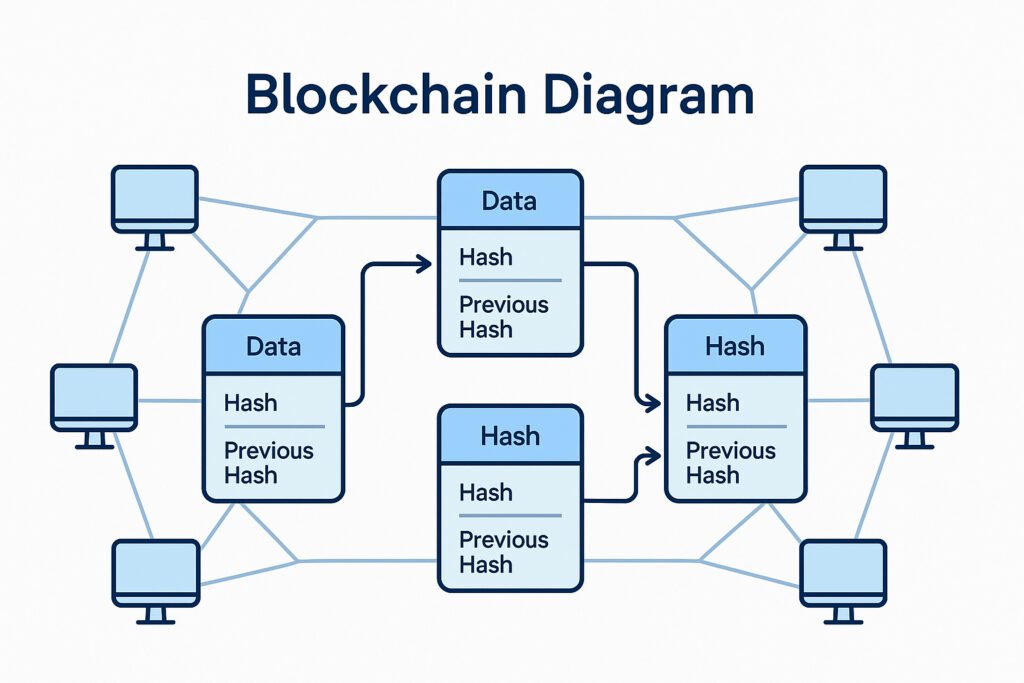
The data itself is secured using a cryptographic hash function, like the famous SHA-256 used by Bitcoin.
- Unique Digital ID: When a new block of transactions is created, all that data (timestamp, transactions, previous block’s hash, etc.) is run through the hash function, which produces a short, unique, fixed-length code—the hash. Think of this hash as the block’s “digital fingerprint.”
- Extreme Sensitivity: The hash is extremely sensitive. If even a single comma or digit in the transaction data is altered, the entire resulting hash changes completely.
- The Chaining Effect: To form the chain, each new block includes the hash of the block that immediately preceded it. This creates an irreversible, secure link. If a hacker tried to change a transaction in a block from five hours ago, they would change that block’s hash. But because the next block is already recorded with the original hash, the network would instantly spot the mismatch, rendering the fraudulent block invalid.
Part 3: The Truth Enforcement (Consensus Mechanisms)

In a decentralized world, how do millions of users who don’t know or trust each other agree on the one single, true version of the ledger? They use Consensus Mechanisms. These are the rules, or algorithms, that govern how transactions are validated and new blocks are added. They are specifically designed to discourage malicious behavior and reward honest participation.
Proof-of-Work (PoW): The Economic Barrier
The most famous consensus mechanism, used by Bitcoin, is Proof-of-Work (PoW).
- The Work: PoW requires specialized computers (Miners) to compete by solving an incredibly complex mathematical problem. This process demands massive amounts of computational power and electricity (the “work”).
- The Reward and the Defense: The first miner to find the solution gets to add the new block to the chain and is rewarded with newly minted cryptocurrency. This high reward incentivizes honest mining. More importantly, this high cost is the defense against attacks. To execute a “51% Attack” (where a single entity gains control of more than half the network’s computing power to alter the ledger), the attacker would have to acquire and maintain more mining equipment and electricity than the rest of the world combined. This makes the attack financially and logistically impossible for a robust network like Bitcoin.
Proof-of-Stake (PoS): The Economic Stake
Newer, more energy-efficient networks like Ethereum use Proof-of-Stake (PoS).
- The Stake: Instead of burning electricity, users (Validators) lock up, or “stake,” their own cryptocurrency as collateral to gain the right to validate new blocks.
- The Reward and the Punishment: Validators are randomly selected to propose and attest to new blocks, and they earn a reward for doing so honestly. Crucially, if a validator tries to approve fraudulent transactions or acts maliciously, their staked crypto is “slashed” (taken away) by the network. This economic punishment—the threat of losing their own valuable assets—makes cheating prohibitively expensive and promotes good behavior.
Part 4: The Permanent Record (Immutability)

The final and most celebrated pillar of blockchain security is Immutability.
Immutability means that once a transaction or piece of data is successfully recorded on the blockchain and validated by the consensus mechanism, it cannot be changed, deleted, or altered, ever.
Transaction Finality
When a block is confirmed and added to the chain, that transaction is considered final. This is a huge shift from traditional finance where transactions can be reversed (chargebacks) or records can be manually edited (e.g., in a government database).
- The Chain of Hash: The mechanism relies entirely on the cryptographic hashing process (Part 2). Because every new block has the hash of the one before it, the entire chain is locked together in a time-stamped sequence. Changing a record in Block #100 would necessitate changing the hash of Block #100, which would then require changing the hash of Block #101, Block #102, and every single block that has been added since.
- Computational Impossibility: The computational power required to recalculate and resubmit the consensus for thousands of blocks in the chain before the honest nodes catch up and reject the fraudulent version is, again, effectively impossible.
This Immutability is what breeds trust. It ensures that the historical record is accurate, permanent, and available for anyone to audit, providing a level of transparency and data integrity that centralized systems simply cannot match.
Conclusion: The Future of Trust
Blockchain technology is not just a passing trend; it is a fundamental breakthrough in digital security and decentralized trust. The system’s robustness comes from the intelligent layering of four core principles:
- Decentralization: Eliminating the single point of failure by distributing the ledger globally.
- Cryptography: Using Public/Private keys to secure ownership and hashing to link blocks immutably.
- Consensus: Employing economic incentives (like PoW and PoS) to make honest validation the only profitable choice.
- Immutability: Ensuring that the transaction history, once recorded, is permanent and tamper-proof.
The result is a digital fortress that protects billions of dollars in digital assets, ensuring transparency, integrity, and security without the need for a trusted middleman. Blockchain has not just secured cryptocurrency; it has provided the blueprint for the future of digital trust itself.
